Securing Critical Infrastructure: Best Practices for Privileged Access Management (PAM)
PAM solutions provide secure access control for critical infrastructure systems
Table of Contents
In today's digital landscape, protecting critical infrastructure is crucial for maintaining the stability of essential services. With increasing cyber threats targeting sectors like energy, banking, and healthcare, managing privileged access to critical systems has become more important than ever. Privileged Access Management (PAM), combined with Bastion Hosts (堡垒机), offers a powerful solution to secure these high-risk systems.
Best Practices for Implementing PAM with Bastion Hosts
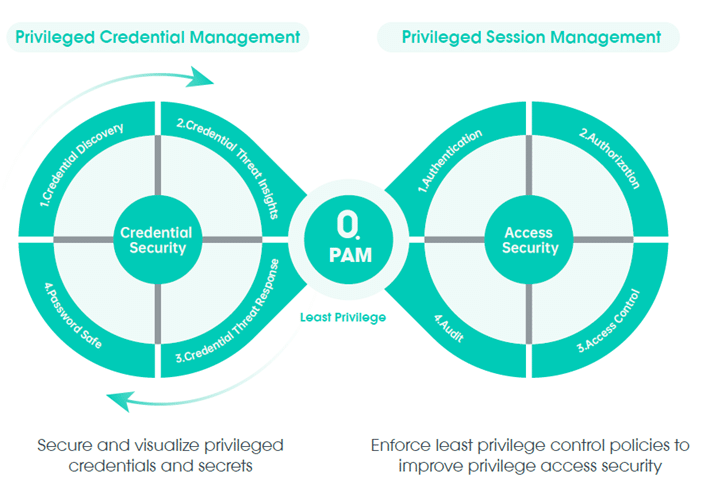
1. Access Control and Account Management
Implementing strict access control is key to securing critical systems. Bastion Hosts act as gateways to ensure that only authorized personnel can access sensitive systems, and that access is limited based on roles and responsibilities.
- Enforce Least Privilege: Only allow users to access what they need to perform their tasks.
- Role-Based Access Control (RBAC): Assign users to specific roles with clearly defined access to critical resources.
- Time-Based Access: Limit access to critical systems during authorized hours.
2. Privileged Access Management
PAM ensures that only the necessary personnel have access to specific administrative capabilities, minimizing the attack surface.
- Just-in-Time Access: Grant temporary, need-based access to critical systems.
- Session Monitoring: Track and record all privileged sessions for auditing and security purposes.
- Granular Access: Limit access to only the systems and functions required for the user's role.
3. Password Management
Password security is crucial in PAM. A strong password policy helps protect privileged accounts from unauthorized access.
- Password Rotation: Automate regular password changes for critical accounts.
- Password Complexity: Enforce strong password policies to prevent easy-to-crack passwords.
- Multi-Factor Authentication (MFA): Add an extra layer of protection by requiring multiple forms of authentication.
Why PAM with Bastion Hosts is Essential
For critical infrastructure operators, ensuring controlled and secure access to sensitive systems is essential to prevent breaches, comply with regulations, and maintain operational integrity. PAM provides an additional layer of security by limiting access to privileged accounts, enforcing strong password policies, and providing comprehensive session auditing.
As threats evolve, having a strong PAM framework integrated with Bastion Hosts is critical for securing your infrastructure and ensuring compliance with security regulations.
"Bastion Host solves data center O&M management, as well as operational audit challenges."
Conclusion
Implementing PAM is a proven strategy to protect critical systems and mitigate risks. By following best practices for access control, privileged access, and password management, you can safeguard your organization's most sensitive resources, improve compliance, and reduce the risk of unauthorized access.
Stay tuned for our next blog post, where we'll dive into real-world PAM use cases and share tips on how to choose the right PAM platform for your organization's needs.
Read more about our Privileged Access Management (PAM) Solution: https://vsceptre.com/featured-solutions/qizhi/
About Vsceptre
At Vsceptre, we connect people with technology. Our team of cybersecurity experts helps organizations implement robust PAM solutions and secure critical infrastructure against evolving cyber threats.
Contact our specialist at charliemok@vsceptre.com to arrange a free one-on-one consultation session.
Related Articles
Validating your cyber defence effectiveness through Breach and Attack Simulation (BAS)
BAS is a proactive approach that automates the process of simulating cyber attacks such as phishing campaigns, malware, or exfiltration.
SecurityThe Shift from Passive Response to Active Validation
Modern cybersecurity is evolving from reactive incident response to proactive threat validation, representing a fundamental paradigm shift.