
Operation Security and Privileged Access Management (PAM)
Command Your Crown Jewels with Absolute Control
Our PAM implementation delivers more than access management—it's a strategic framework that proactively secures your most critical assets, ensuring every privileged action is authorized, monitored, and audit-ready.
Strategic PAM Architecture & Implementation Roadmap
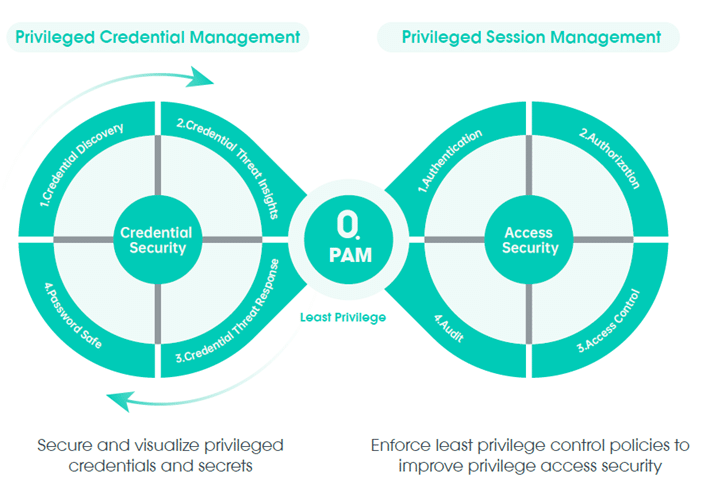
Enterprise Credential Vaulting & Automated Rotation
Privileged Access MFA Integration
Privileged Session Monitoring & Recording
Compliance Reporting & Audit Preparedness
Lock Down Your Crown Jewels, We'll Guard the Gates
Our comprehensive PAM program assumes full ownership of your privileged access security, ensuring your team can innovate without compromise.
Discover & Classify
Comprehensive discovery and classification of all privileged accounts and access pathways across your environment, eliminating unknown vulnerabilities and shadow access points.
Secure & Vault
Hardened vault implementation with enforced credential rotation policies, preventing credential theft through secure storage and automated refresh cycles.
Control & Authenticate
MFA integration and just-in-time access workflows, ensuring every privileged session requires multi-factor verification and temporary elevation approval.
Monitor & Record
Real-time privileged session monitoring with full recording capabilities, detecting anomalies and creating complete audit trails for compliance needs.
Govern & Optimize
Regular governance reviews and continuous improvements, ensuring your PAM framework evolves with both emerging threats and business changes.
Your Key Benefits
Reduced Breach Risk
Minimize both internal and external threat vectors through strict privileged access controls.
Streamlined Administration
Simplify and accelerate privileged access workflows for IT teams without compromising security.
Compliance Assurance
Generate detailed, compliant audit trails for regulatory requirements and internal reviews.
Scalable Foundation
Deploy a flexible PAM solution that grows with your business across any infrastructure environment.
Why Choose Vsceptre
Cutting-Edge Technology
Leverage our strategic partnership with Qizhi for industry-leading PAM technology and innovation.
Compliance Expertise
Benefit from our deep specialization in designing and implementing fully compliant PAM frameworks.
24/7 Support
Access round-the-clock technical assistance and ongoing optimization for continuous protection.
Ready to Lock Down Your Privileged Access?
Contact our cybersecurity specialists for a confidential PAM assessment. Let's build a framework that protects your most critical assets while maintaining operational agility.
Request a PAM ConsultationPrefer to talk first? Speak directly with an expert: +852 2889 1088