
Vulnerability Assessment & Adversarial Exposure Validation (AEV)
Expose Critical Vulnerabilities Before Attackers Exploit Them
Our Vulnerability Assessment & AEV service delivers more than standard scanning—it's a continuous security validation framework that identifies, prioritizes, and verifies remediation of critical weaknesses, ensuring you fix what matters most before attackers can exploit them.
Continuous Automated Vulnerability Discovery & Scanning
Real-World Adversarial Attack Simulation & Penetration Testing
Risk-Based Vulnerability Prioritization & Cyber Risk Management
Actionable Remediation Roadmaps & Compliance Guidance
Verification Testing & Proof-of-Fix Validation
Identify Every Security Gap, We'll Verify Your Defenses
Our integrated validation services deliver continuous security assurance, empowering your team to innovate while maintaining robust protection against evolving threats.
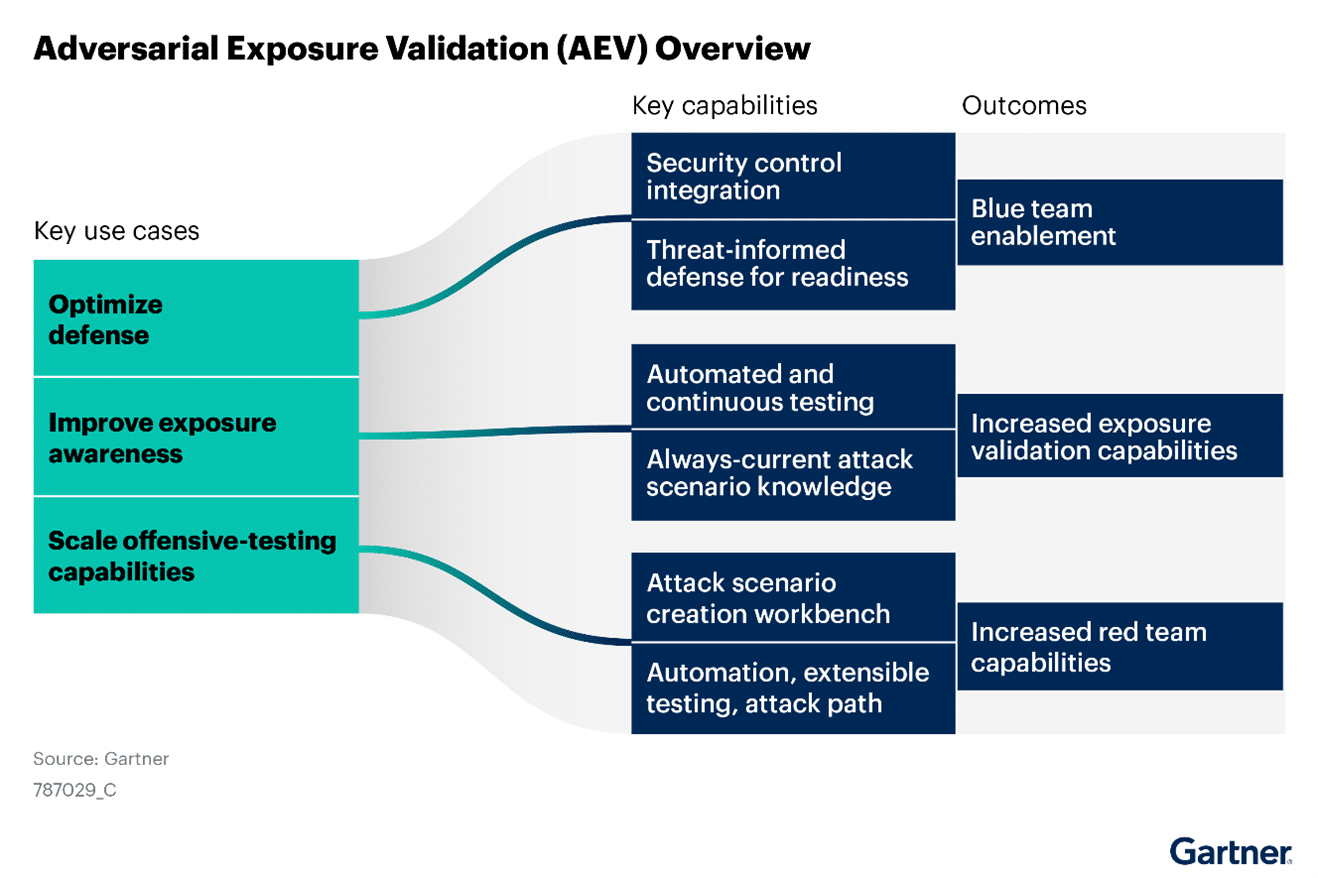
Gartner's Market Guide for Adversarial Exposure Validation (March 2025)
Discover & Assess
Comprehensive discovery and continuous security scanning across your entire digital environment, including third-party risk management and supply chain security components, through automated 24/7 monitoring.
Simulate & Test
Real-world adversarial simulation exercises and penetration testing services that replicate actual threat actor techniques, validating your security controls against current exploitation methods and attack vectors.
Analyze & Prioritize
Risk-based analysis and business impact assessment aligned with cyber risk management frameworks, delivering actionable remediation guidance prioritized by exploitability and compliance requirements.
Remediate & Verify
Guided remediation support and proof-of-fix validation through comprehensive retesting, ensuring vulnerabilities are fully resolved while providing documented evidence for audit and regulatory compliance.
Monitor & Improve
Ongoing security metrics through our integrated SIEM and Security Scorecard platform, continuously tracking your security posture and driving measurable improvements for long-term digital resilience.
Your Key Benefits
Proactive Threat Exposure Management
Identify critical security weaknesses across your infrastructure before attackers can exploit them, reducing potential business impact and recovery costs significantly.
Risk-Based Vulnerability Prioritization
Focus security resources on high-impact vulnerabilities with clear exploitability ratings, optimizing your security investment for maximum ROI and protection.
Accelerated Remediation Cycles
Reduce exposure windows and mean-time-to-remediation with actionable guidance and verification testing that streamlines your security fix processes.
Continuous Security Validation
Demonstrate tangible security posture improvements through ongoing metrics and compliance evidence, supporting audit requirements and stakeholder confidence.
Why Choose Vsceptre
Integrated Validation Platform
Leverage our Security Scorecard platform combined with SIEM and SOAR capabilities for continuous visibility and measurable security improvements across your environment.
Expert Adversarial Testing
Benefit from our team's real-world attack simulation expertise, delivering managed detection and response insights that go beyond automated scanning.
Complete Program Ownership
Ensure comprehensive coverage from initial assessment through verification with single-source accountability for your vulnerability assessment and adversarial exposure validation needs.
Ready to Transform Your Cybersecurity Posture?
Connect with our cybersecurity specialists for a confidential exposure assessment. Let's establish a proactive defense framework that identifies and neutralizes critical risks before they impact your business.
Start Your Security ValidationPrefer to talk first? Speak directly with an expert: +852 2889 1088