The Shift from Passive Response to Active Validation
Adversarial Exposure Validation (AEV) technology helps organizations validate their defensive posture against attack scenarios and techniques. It enhances exposure awareness, improves attack scenario readiness, and supports continuous threat exposure management. AEV solutions offer diverse approaches, including automation and integration capabilities, to optimize investments in security technologies, processes, and human resources. Frequent validation testing is recommended to manage exposure effectively.
Gartner's Market Guide for Adversarial Exposure Validation (March 2025) highlights critical changes in cybersecurity validation. This article explores the key findings and their implications for security strategies, emphasizing the necessity of continuous threat exposure validation in modern defenses.
The evolution from reactive security measures to proactive validation represents a paradigm shift in cybersecurity
Table of Contents
01 Market Evolution: From BAS to AEV
Gartner's report signifies a pivotal evolution in cybersecurity validation, as vulnerability assessment, automated penetration testing, and red-teaming converge into Adversarial Exposure Validation (AEV). This shift addresses real-world challenges: merely identifying vulnerabilities is insufficient. Organizations must confirm exploitability and understand the impact in their unique environments.
Key Market Insights
- • Market Growth: By 2027, Gartner forecasts that 40% of organizations will adopt formal exposure validation programs
- • Convergence Trend: Vulnerability assessment, automated penetration testing, and red-teaming are converging into AEV
- • Real-world Focus: Organizations must confirm exploitability and understand impact in their unique environments
- • Substantial Growth: The report indicates substantial growth potential in the AEV market
- • Strategic Shift: Moving from reactive vulnerability identification to proactive validation
02 Core Use Cases of AEV
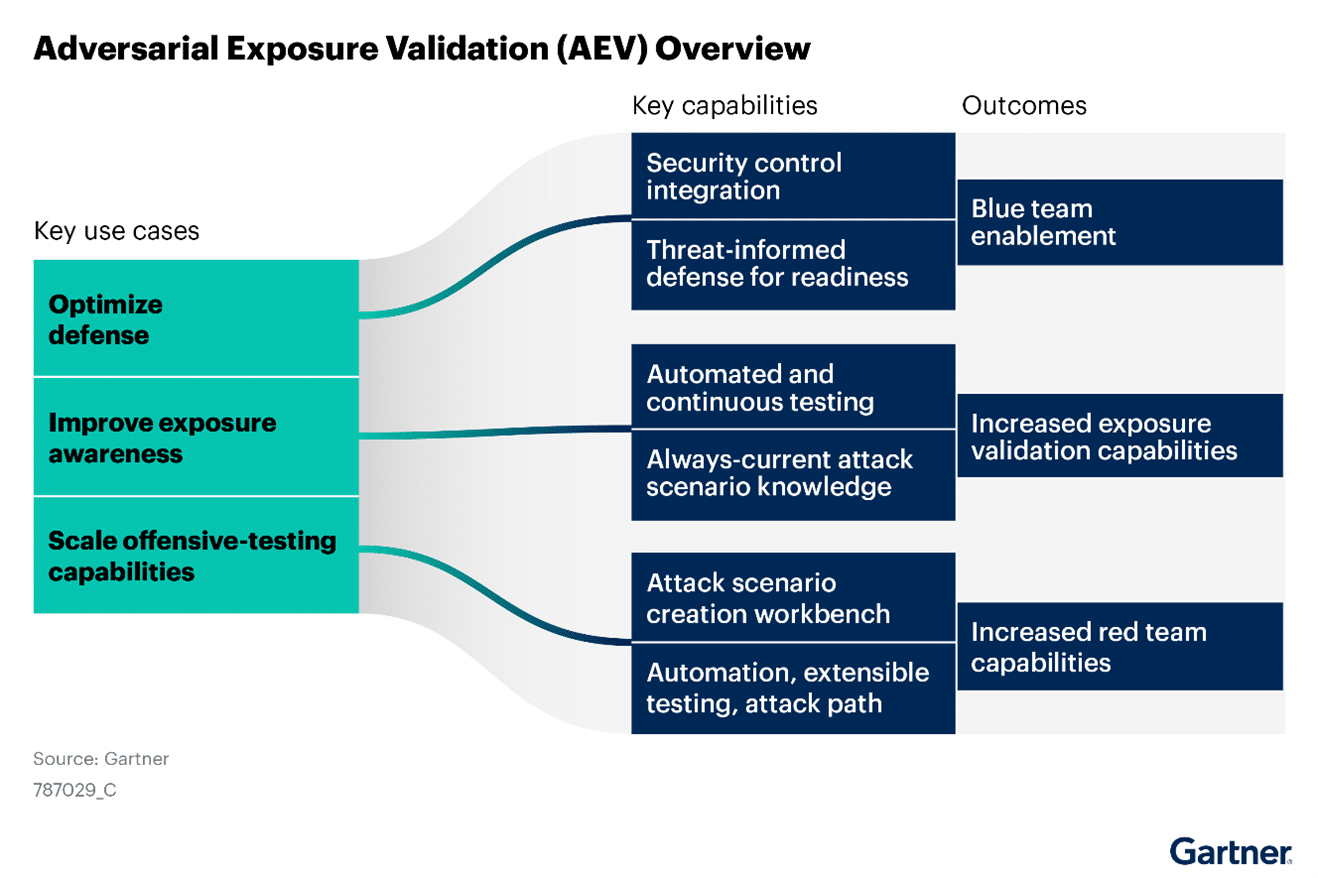
Gartner identifies three primary use cases for AEV solutions, emphasizing their role in enhancing risk management and operational efficiency. These use cases include optimizing defense posture, improving exposure awareness, and expanding offensive testing capabilities. By addressing these areas, AEV solutions enable organizations to not only identify and validate vulnerabilities but also adapt their security strategies to evolving threats.
Optimize Defense Posture
- • Validation of Security Controls: Assess existing defenses against known threats
- • Optimization Suggestions: Tailor recommendations for specific vendor controls
- • Trend Data Generation: Track improvements in defense posture
Enhance Exposure Awareness
- • Vulnerability Confirmation: Filter and validate potential vulnerabilities
- • Contextual Exposure Mapping: Prioritize vulnerabilities based on real attack paths
- • Linking Security Testing to Business Impact: Allocate resources more effectively
Expand Offensive Testing Capabilities
- • Automated Attack Scenarios: Use an automated workbench to create complex tests
- • Increased Red Team Productivity: Enhance testing coverage without additional personnel
- • Threat Intelligence Integration: Seamlessly incorporate intelligence into testing
03 The Unique Value of AEV
AEV solutions provide distinct advantages over traditional exposure assessment platforms, offering validation over theory, automation and consistency, and bridging offense and defense capabilities.
Validation over Theory
AEV solutions go beyond theoretical vulnerability assessments by providing real-world validation of security controls and attack scenarios.
- Closed-Loop Validation: Confirm vulnerabilities in real environments
- Scenario Creation: Test security controls against practical attack scenarios
- Real-world Testing: Validate defenses against actual threat techniques
- Impact Assessment: Understand the true business impact of vulnerabilities
Automation and Consistency
AEV solutions enable frequent, consistent testing without requiring extensive security expertise, providing comparable results over time.
- Frequent Testing: Achieve regular assessments without extensive expertise
- Comparable Results: Measure security improvements consistently
- Automated Workflows: Reduce manual effort and human error
- Scalable Operations: Test across multiple environments efficiently
Bridging Offense and Defense
AEV solutions promote collaboration between red and blue teams while providing quantifiable data to validate security investments.
- Collaboration Promotion: Enhance insights between blue and red teams
- Quantifiable Data: Validate the effectiveness of security investments
- Unified Approach: Combine offensive and defensive perspectives
- Continuous Improvement: Enable iterative security enhancement
04 Practical Steps for Implementing AEV
Organizations should take clear steps to improve cybersecurity validation. This includes using real-world attack scenarios and advanced tools to find weaknesses and strengthen defenses against evolving threats.

AEV Overview: Key use cases, capabilities, and outcomes (Source: Gartner)
05 Cyritex Cybersecurity Validation Platform: A Leading AEV Solution in China
As a pioneer in China's cybersecurity validation market, Cyritex offers an AI-powered platform that aligns with Gartner's core use cases. Utilizing real-world attack scenarios and advanced AI, Cyritex provides comprehensive exposure validation, identifying weaknesses and suggesting mitigation strategies based on actual data.
Platform Capabilities
- AI-powered threat simulation and validation
- Real-world attack scenario testing
- Comprehensive exposure validation
- Automated mitigation strategy recommendations
Market Position
- Pioneer in China's cybersecurity validation market
- Aligns with Gartner's core AEV use cases
- Advanced AI and machine learning integration
- Data-driven security insights and recommendations
Vsceptre Partnership
Vsceptre serves as the implementation partner for the Cyritex Cybersecurity Validation Platform. For more information on building a robust security validation solution, please contact us at:
charliemok@vsceptre.com
06 Conclusion
The evolution of cybersecurity validation from reactive measures to proactive validation represents a paradigm shift. The Cyritex Cybersecurity Validation Platform empowers organizations to enhance their defenses, ensuring they are equipped to face evolving threats effectively.
As cyber threats continue to evolve in sophistication and frequency, the shift toward active validation becomes not just advantageous but essential. Organizations that embrace this proactive approach will be better positioned to defend against emerging threats and maintain robust security postures in an increasingly complex digital landscape.
Key Strategic Takeaways
- • AEV represents a paradigm shift from reactive to proactive cybersecurity validation
- • Continuous testing and validation prevent threats before they materialize
- • Implementation requires strategic planning and phased execution
- • Organizations must invest in automation and threat intelligence capabilities
- • Future security success depends on embracing proactive methodologies
- • The shift delivers measurable improvements in security and business outcomes
About Vsceptre
Vsceptre specializes in observability solutions and DevOps best practices. Our team of experts helps organizations implement robust monitoring, feature management, and application reliability solutions to minimize downtime and enhance user experience.
For further information, contact Vsceptre at charliemok@vsceptre.com
Related Articles
Validating your cyber defence effectiveness through Breach and Attack Simulation (BAS)
BAS is a proactive approach that automates the process of simulating cyber attacks such as phishing campaigns, malware, or exfiltration, to name a few, and then evaluates the organization's defences.
SecuritySecuring Critical Infrastructure: Best Practices for Privileged Access Management (PAM)
In today's digital landscape, protecting critical infrastructure is crucial for maintaining the stability of essential services. With increasing cyber threats targeting sectors like energy, banking, and healthcare, managing privileged access to critical systems has become more important than ever.